Security is a critical component of keeping the information on your computer safe. In the early days of personal computing, that meant using a virus scanner. While having an up to date anti-virus program is a good first step, today you must take additional precautions to ensure the safety of your computer and its contents.
Viruses are actually a diminishing part of malware—malicious software designed to infiltrate a computer. They used to be the most popular way of infecting PCs from email. Users have become very proficient at blocking viruses, especially those shared via e-mail. Now malware writers are turning to other ways of infecting your computer.
Other Methods?
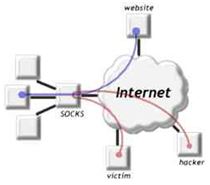 One popular way to infect a computer is by opening a door. The doors are called ports on your computer. While connected to the Internet, certain ports are open to send and receive data and other ports are open to send and receive e-mail. Some ports are open to perform other functions. Malware writers use these open ports to drop bots or Web Robots that can run an automated attack on networked computers. This attack can be run immediately or as a payload activated at a future date and time. Another method of infection is Trojans (or Trojan horses). Trojans appear to provide a desirable function or software for the end user, but instead provide unauthorized access to the user’s computer system and may even install other malware on your computer.
One popular way to infect a computer is by opening a door. The doors are called ports on your computer. While connected to the Internet, certain ports are open to send and receive data and other ports are open to send and receive e-mail. Some ports are open to perform other functions. Malware writers use these open ports to drop bots or Web Robots that can run an automated attack on networked computers. This attack can be run immediately or as a payload activated at a future date and time. Another method of infection is Trojans (or Trojan horses). Trojans appear to provide a desirable function or software for the end user, but instead provide unauthorized access to the user’s computer system and may even install other malware on your computer.
How Does This Happen?
 Most office environments have hardware firewalls in place, either provided by the local IT departments or by the vendor providing Internet access (AT&T, EarthLink Business, Verizon, etc.) So how does infection happen? More than likely, the infection occurs when you take the computer in the road. Internet connections at home provided by cable modems from carriers like Comcast or Time-Warner rarely have security in place for users. If you connect your machine at home, you should have a firewall program running local on your PC. It is also important to have firewall security if you are connecting to a public Wi-Fi hotspot. Locations such as coffee shops, fast food restaurants and airports provide access for the convenience of travelers. They make them easy to connect. That ease of connection can also affect security. Never assume that anything you connect to is secure unless you know it is!
Most office environments have hardware firewalls in place, either provided by the local IT departments or by the vendor providing Internet access (AT&T, EarthLink Business, Verizon, etc.) So how does infection happen? More than likely, the infection occurs when you take the computer in the road. Internet connections at home provided by cable modems from carriers like Comcast or Time-Warner rarely have security in place for users. If you connect your machine at home, you should have a firewall program running local on your PC. It is also important to have firewall security if you are connecting to a public Wi-Fi hotspot. Locations such as coffee shops, fast food restaurants and airports provide access for the convenience of travelers. They make them easy to connect. That ease of connection can also affect security. Never assume that anything you connect to is secure unless you know it is!
Security
 Security sets us free to do what we do best. It’s simple and mostly common sense. Make sure you let co-workers, your family and friends know what to do too, so they’re safe online. Security is the responsibility of us all. Sophos put together a list of ten items that can help with computer safety and that of work networks and data.
Security sets us free to do what we do best. It’s simple and mostly common sense. Make sure you let co-workers, your family and friends know what to do too, so they’re safe online. Security is the responsibility of us all. Sophos put together a list of ten items that can help with computer safety and that of work networks and data.
- Don’t be tricked into giving away confidential information
Don’t respond to emails or phone calls requesting confidential company information including employee information, financial results or company secrets. It’s easy for an unauthorized person to call us and pretend to be an employee or one of our business partners. Stay on guard to avoid falling for this scam, and report any suspicious activity to IT. Protect your personal information just as closely. - Don't use an unprotected computer
When you access sensitive information from a non-secure computer, like one in an Internet café or a shared machine at home, you put the information you're viewing at risk. Make sure your computer is running the latest approved security patches, antivirus and firewall. - Don't leave sensitive info around the office
Don't leave printouts containing private information on your desk. Lock them in a drawer or shred them. It's very easy for a visitor to glance down at your desk and see sensitive documents. Keep your desk tidy and documents locked away. It makes the office look more organized, and reduces the risk of information leaks. - Lock your computer and mobile phone when not in use
Always lock your computer and mobile phone when you're not using them. You work on important things, and we want to make sure they stay safe and secure. Locking your phone and computer keeps your data and contacts safe from prying eyes. - Stay alert and report suspicious activity
Always report any suspicious activity to your IT team. Part of their job is to stop cyber-attacks and to make sure that company data or intellectual property isn't lost or stolen. In business, everyone’s job depends on keeping that information safe. In case something goes wrong, the faster your company knows about it, the faster they can deal with it. - Password-protect sensitive files and devices
Always password-protect sensitive files on your computer, USB flash drive, smartphone, laptops, etc. Losing a device can happen to anyone. Protecting your device with strong passwords means you make it incredibly difficult for someone to break in and steal data. You may have a policy that allows or denies password protecting files. This is often something that is not done if other network drives are assigned with specific permissions to protect files from access except for specific users and departments. - Always use hard-to-guess passwords
Don't use obvious passwords like "password," "cat," or obvious character sequences on the qwerty keyboard like "asdfg" and "12345." It's better to use complex passwords. Include different letter cases, numbers and even punctuation. Try to use different passwords for different websites and computers. So if one gets hacked, your other accounts aren't compromised. If your IT department assigns you passwords that seem cryptic, they are doing a good job! - Be cautious of suspicious emails and links
Don’t let curiosity get the best of you. Always delete suspicious emails and links. Even opening or viewing these emails and links can compromise your computer and create unwanted problems without your knowledge, especially if you use a preview pane in Outlook (not a good idea). Remember, if something looks too good to be true, it probably is. - Don’t plug in personal devices without the OK from IT
Don’t plug in personal devices like USB flash drives, MP3 players and smartphones without permission from IT. In all likelihood, you should have a company policy that deals with computing devices or BYOD (bring your own device). These devices can be compromised with code waiting to launch as soon as you plug them into a computer. Talk to IT about your devices and let us make the call. - Don’t install unauthorized programs on your work computer
Malicious applications often pose as legitimate programs, like games, tools or even antivirus software. They aim to fool you into infecting your computer or network. If you like an application and think it will be useful, contact IT to look into it before installing.
For More Information
Sophos also has ten one-minute videos for each bullet item that expand firther with real world examples of the items in the above list. They are worth a view, especially if it does not violate your company’s Internet use policy (yes, you should have one of those too)!
Videos: One-minute tips
- Tip 1: Don't get tricked
- Tip 2: Stay secure
- Tip 3: Put things away
- Tip 4: Lock it
- Tip 5: Stay alert
- Tip 6: Protect it
- Tip 7: Good passwords
- Tip 8: Think first
- Tip 9: Don't plug it in
- Tip 10: Don't install it
Have A Question Or Comment?
We always like to get your feedback. After all, helping you to understand the issue at hand or new technology will result in better decisions, better connectivity, increased productivity and ultimately better security for hardware and software environments! If you have questions or comments about this article, contact me (JohnBoline@hagerman.com).


Comments