Remember when you had to click the “Accept” or “OK” button three or four times before you could download a piece of software? It seemed as though you had to click that button a dozen times to confirm you really wanted to download a program. Gone are the good old days when you had to click a button to download or install a software update in order to become infected. Just opening a compromised web page in your browser of choice can now allow dangerous code to install on your device. This kind of attack happens all the time. But you don’t have to be a victim. How can you stop this from happening to you? Read on!
What is a Drive-By Download?
 A drive-by download refers to the unintentional download of a virus or malicious software (malware) onto your computer or mobile device. Web pages are the number one source of “malicious software” or malware. The majority of these malware threats come from what is called a drive-by download. All you need to do is visit or “drive by” a web page without stopping to click or accept any software and the malicious code can download in the background to your device. A drive-by download will usually take advantage of a browser, app, or operating system that is out of date and has a security flaw to exploit these weaknesses. The initial code that is downloaded is often very small. That code has a simple job -- to contact another computer where it can pull down the rest of the code onto your smartphone, tablet, or computer. Often, a web page will contain several different types of malicious code in hopes that one of them will match a weakness on your computer.
A drive-by download refers to the unintentional download of a virus or malicious software (malware) onto your computer or mobile device. Web pages are the number one source of “malicious software” or malware. The majority of these malware threats come from what is called a drive-by download. All you need to do is visit or “drive by” a web page without stopping to click or accept any software and the malicious code can download in the background to your device. A drive-by download will usually take advantage of a browser, app, or operating system that is out of date and has a security flaw to exploit these weaknesses. The initial code that is downloaded is often very small. That code has a simple job -- to contact another computer where it can pull down the rest of the code onto your smartphone, tablet, or computer. Often, a web page will contain several different types of malicious code in hopes that one of them will match a weakness on your computer.
What Kind of Websites have Drive-By Downloads?
People often assume that an infected website will be one with an illegal download, pornography, etc. While that can be the case, these downloads are more often placed on otherwise innocent and normal-looking websites. As noted in my 2014 article “Dangerous Downloads”, the HP site for driver downloads was compromised with such content. Today’s threats use a layered approach to infect your PC. You might receive a link in an email, text message, or social media post that tells you to look at something interesting on a site. When you open the page, while you are enjoying the article or cartoon, the download is installing on your computer. Still, other threats may come from advertisements that rotate from other sites that are not directly hosted on the website you have accessed.
Tracking Malicious Behavior
 As noted by Intel / McAfee Security, researchers detect drive-by downloads by keeping track of web addresses that they know have a history of malicious or suspicious behavior. In order to track this malicious behavior, security firms use crawlers or spiders to wander the Web and visit different pages. If a web page initiates a download on a test computer, the site is given a risky reputation. In order to avoid infection, there are some sites that you should avoid, which include file-sharing websites and those with adult content. As long as your computer is secure, it should be safe to search most of the web. You should have your firewall active, anti-virus software that is running and up-to-date, and some sort of anti-malware software. Additional countermeasures that block content of a particular type (e.g. adult content, etc.) like OpenDNS can also be applied even to home networks. By their very nature, some types of sites (e.g., adult content, warez, etc.) are more likely to include malware, but even legitimate sites might be unknowingly compromised. Norton and other locations can do a ‘scan’ of a website to see if there are any known threats that have been reported for a particular website. There are also sites that will allow you to put in a URL and have it scanned, particularly useful in the case of a file download, so that you can identify if the file is carrying a malicious payload.
As noted by Intel / McAfee Security, researchers detect drive-by downloads by keeping track of web addresses that they know have a history of malicious or suspicious behavior. In order to track this malicious behavior, security firms use crawlers or spiders to wander the Web and visit different pages. If a web page initiates a download on a test computer, the site is given a risky reputation. In order to avoid infection, there are some sites that you should avoid, which include file-sharing websites and those with adult content. As long as your computer is secure, it should be safe to search most of the web. You should have your firewall active, anti-virus software that is running and up-to-date, and some sort of anti-malware software. Additional countermeasures that block content of a particular type (e.g. adult content, etc.) like OpenDNS can also be applied even to home networks. By their very nature, some types of sites (e.g., adult content, warez, etc.) are more likely to include malware, but even legitimate sites might be unknowingly compromised. Norton and other locations can do a ‘scan’ of a website to see if there are any known threats that have been reported for a particular website. There are also sites that will allow you to put in a URL and have it scanned, particularly useful in the case of a file download, so that you can identify if the file is carrying a malicious payload.
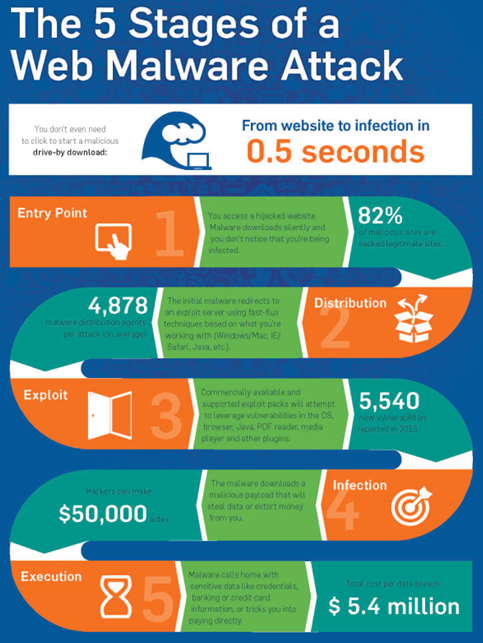
Anatomy of a Drive-by Download
There are five stages of a web attack that compose the anatomy of a drive-by download. As previously mentioned, a drive-by download describes how malware can infect your computer simply by visiting a website that is running malicious code. This is known as Stage 1, or the Entry Point. Most of the time, these are legitimate websites that have been compromised to redirect you to another site controlled by the hackers. Once there, Stage 2, or the distribution phase of a drive-by, commences. Often, cybercriminals will use sophisticated malware packaged in an “exploit kit” that can find a vulnerability in your software from thousands of possibilities. Once the exploit kit finds a security vulnerability in any software on your system that it can attack, Stage 3, or the exploit phase, begins. Once the exploit kit has identified a security vulnerability on the system, that is when Stage 4, or the infection of the system, begins. During the infection phase of an attack, the “payload” is downloaded to your system and the malware installs itself on your computer. Once it is installed, Stage 5, or the execution of the malware, begins and does what it was designed to do, which is mainly to make money for its masters. Depending on the type of infection and payload, your email could be compromised, bank records accessed, and even ransomware can be loaded that will hold your files hostage until you pay to have them released. For more information about Ransomware see my article on the subject from June 2016. Sophos produced this chart (below) that shows just how fast this entire process can take place.
Securing the Web
It takes planning and diligent follow-up to make sure your system(s) stay safe. In order to keep infection from your system, you can follow a few simple steps:
- Keep your operating system up to date
- Keep your applications up to date
- Keep your browser(s) up to date
- Install and keep your anti-virus up to date
- Install and keep your anti-malware up to date
- Use web filtering:
- Something like Open DNS for home
- Something like Dell SonicWALL for business
- Scan your system for threats on a regular basis
- Backup your data regularly
As Sophos notes on their website in an article from 2014 by John Zorabedian, these kinds of attacks happen all the time, but you don’t have to be a victim. Following industry best practices can keep you on the leading edge of safe computing.
Breaking Tech Practices
The purpose of this article is to make you aware of the best tech practices to keep you and your data safe. Keeping an eye on the mix of patches, appliances, and software for protecting your data, while keeping backups of your data, will pay dividends should you have a problem with an infection on your computer or your enterprise. If you have questions or comments about this article, contact me.


Comments