While installations of many different operating systems exist, such as those produced by Apple, many flavors of Linux and others, I am going to demonstrate how to harden a Windows installation. Why? In spite of what you read, when it comes to laptops, 2 in 1’s, Desktop and Tower systems and Servers, be they rack mounted, virtual or cloud-based, there are simply more installations of Microsoft Windows. More installations of an operating system mean that the potential for attack is larger because there is a larger audience. There are some very simple things that can be done to harden your systems, whether you are an IT Professional or are protecting your system at home. Let’s get started!
What is System Hardening?
 System hardening, also called Operating System hardening, helps minimize security vulnerabilities. Most computers, no matter the operating system, offer network security features to limit outside access to the system. Common programs that do this include Firewall Software, Antivirus programs and Spyware blockers. Each of these has their place in preventing malicious software from running on the machine. Even with these security measures in place, computers are often still vulnerable to outside access. The purpose of system hardening is to eliminate as many security risks as possible. This is typically done by removing all non-essential software programs and utilities from the computer.
System hardening, also called Operating System hardening, helps minimize security vulnerabilities. Most computers, no matter the operating system, offer network security features to limit outside access to the system. Common programs that do this include Firewall Software, Antivirus programs and Spyware blockers. Each of these has their place in preventing malicious software from running on the machine. Even with these security measures in place, computers are often still vulnerable to outside access. The purpose of system hardening is to eliminate as many security risks as possible. This is typically done by removing all non-essential software programs and utilities from the computer.
What is Involved in System Hardening?
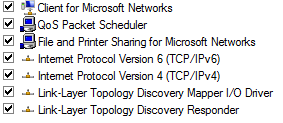 In order to harden a system, the attack surface should be minimized. This includes everything from reducing permissions where possible to eliminating default user accounts that can open the system to vulnerability. For example, by default, windows enables the following network protocols and add-ins when you perform an operating system installation. There may be even more add-ins, like Apple Talk, etc. In most cases, you can actually go in and turn off items that are not in use. For example, the vast majority of installations do not use TCP/IPv6, so having it enabled allows another available attack surface that is not required. The same would go for Apple Talk. If you are not using it in your environment, turn it off.
In order to harden a system, the attack surface should be minimized. This includes everything from reducing permissions where possible to eliminating default user accounts that can open the system to vulnerability. For example, by default, windows enables the following network protocols and add-ins when you perform an operating system installation. There may be even more add-ins, like Apple Talk, etc. In most cases, you can actually go in and turn off items that are not in use. For example, the vast majority of installations do not use TCP/IPv6, so having it enabled allows another available attack surface that is not required. The same would go for Apple Talk. If you are not using it in your environment, turn it off.
Least Privilege and Reducing Attack Surface
 Another of the main concepts in hardening is running a system with the least privilege required. That means your system is configured so that it is only capable of doing things you normally do, and nothing else. That means that if a feature in Windows is not used, it is to be turned off, or disabled. The reason behind doing this is that the more features you have enabled, the larger your attack surface is and the more you have to defend. One vulnerable spot is all it takes to get hacked, therefore the more features you have, the more potential bugs ( some security related ) you have. We know that attackers exploit security bugs in the system – that’s how they attack. If you go live on the internet with all features turned on, the attacker would have a lot of choices. If you disable unused features, then they’d have less to play with.
Another of the main concepts in hardening is running a system with the least privilege required. That means your system is configured so that it is only capable of doing things you normally do, and nothing else. That means that if a feature in Windows is not used, it is to be turned off, or disabled. The reason behind doing this is that the more features you have enabled, the larger your attack surface is and the more you have to defend. One vulnerable spot is all it takes to get hacked, therefore the more features you have, the more potential bugs ( some security related ) you have. We know that attackers exploit security bugs in the system – that’s how they attack. If you go live on the internet with all features turned on, the attacker would have a lot of choices. If you disable unused features, then they’d have less to play with.
One of the first things you should do in line with least privilege is to create a Standard user account and use it for your daily work. Only login to the administrative account to install programs, configure networking, or do system maintenance tasks. When you are working in a Standard account, any malware or hacker that makes it onto your system will inherit your privilege and not have administrative privileges to make system-wide modifications. And that’s a win for you.
What About Cloud Storage?
 Although the cloud remains for many something of an unknown quantity as far as security is concerned, the truth is that data security is never a black and white issue. If, for example, you give your ‘cloud-folder’ full rights, then if an attacker were to place a file or files in your folder, you would open your system to attack. That would not be the case if you use a different, more secure password for that storage that is different from the credentials you use to surf the web. You do that, right? Secure data storage will never be 100% secure as long as people use it! One of the best lines I have heard in this regard is from Davey Winder at ALPHR.com who said: “…that attaining a 100% secure data storage solution is akin to grabbing your shadow; you can get very close but will never actually do it.” For consumers and most small business users who are not subject to regulatory restrictions, the cloud is actually pretty secure these days. Just about every cloud store will encrypt data in transit. While data not being encrypted at rest, or if it is then the cloud provider managing the keys, does mean that the data can be indexed, de-duplicated, compressed and easily restored in a worse-case scenario. It also means that your data isn't as secure as it might otherwise be.
Although the cloud remains for many something of an unknown quantity as far as security is concerned, the truth is that data security is never a black and white issue. If, for example, you give your ‘cloud-folder’ full rights, then if an attacker were to place a file or files in your folder, you would open your system to attack. That would not be the case if you use a different, more secure password for that storage that is different from the credentials you use to surf the web. You do that, right? Secure data storage will never be 100% secure as long as people use it! One of the best lines I have heard in this regard is from Davey Winder at ALPHR.com who said: “…that attaining a 100% secure data storage solution is akin to grabbing your shadow; you can get very close but will never actually do it.” For consumers and most small business users who are not subject to regulatory restrictions, the cloud is actually pretty secure these days. Just about every cloud store will encrypt data in transit. While data not being encrypted at rest, or if it is then the cloud provider managing the keys, does mean that the data can be indexed, de-duplicated, compressed and easily restored in a worse-case scenario. It also means that your data isn't as secure as it might otherwise be.
Breaking Security Practices
The purpose of this article is to make you aware of some of the best tech practices to get a baseline set for security with your operating system. This will help keep you and your data safe. Everything fits and works together, so keep an eye on the mix of patches, appliances, and software you run to help protect system and data security. Backup early and often because keeping backups of your data will pay dividends should you have a problem with an infection on your computer or your enterprise. If you have questions or comments about this article, contact me.


Comments